IDOR Vulnerability on JobsDB
Background
Every time an applicant applies for a job, an email is sent to the employer containing links to shortlist/reject a candidate.
Pressing on the link takes the employer to an listing the applicant's email and phone number.
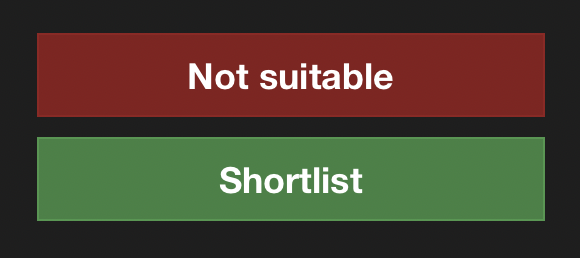
Links in the system-generated email
Vulnerability
The endpoint relies on the jobApplicationId parameter to return the applicant's personal details, but the endpoint fails to authenticate the request, or verify whether or not the jobApplicationId parameter corresponds to a certain employerID,.
Prerequesites
An attacker is able to exploit this vulnerability by crafting a URL using a valid employerId and jobApplicationId
Impact
An unauthorized user could potentially:
- access personal information of unrelated candidate
- scrape and publicize customer data
POC
Visit https://rms.jobsdb.com/hk/EN/emphome/UpdateCandidateStatusSuccess?employerId=1234****&jobApplicationId=1234****&updatedStatusId=2&candidateType=1
Increment the jobApplicationId parameter in the URL by 1
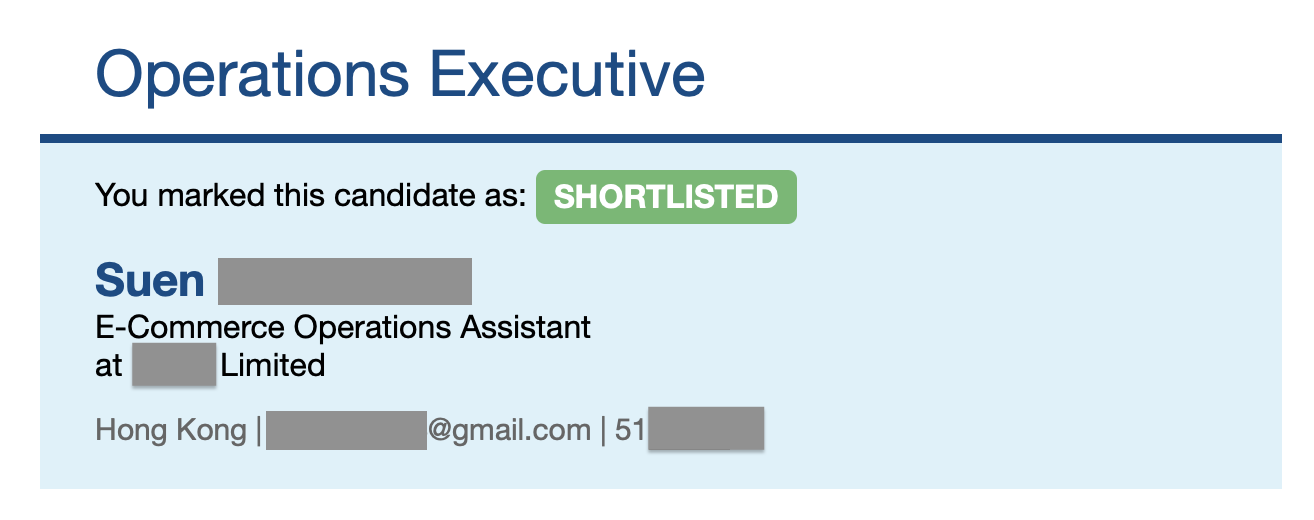
Potential exposure of an applicant's location, email address, telephone number and job title
Timeline
Issued reported to JobsDB on 2020/06/16
Patched on 2020/06/24